What better way to get into the festive mood then by taking part in an awesome online security conference – KringleCon 2019 from the SANS institute. For anyone new it’s a free online conference which includes youtube hosted presentations from security professionals on a variety of topics as well as a CTF game where you help Santa figure out who has stolen two turtle doves from elf university!

How to Join?
It’s a free conference, to join in the fun simply visit HolidayHackChallenge 2019 and click on Kringlecon2 at the top then register an account. If you just want to listen to the talks you can see them all on their YouTube channel : YouTube – Kringlecon2
CTF Challenges
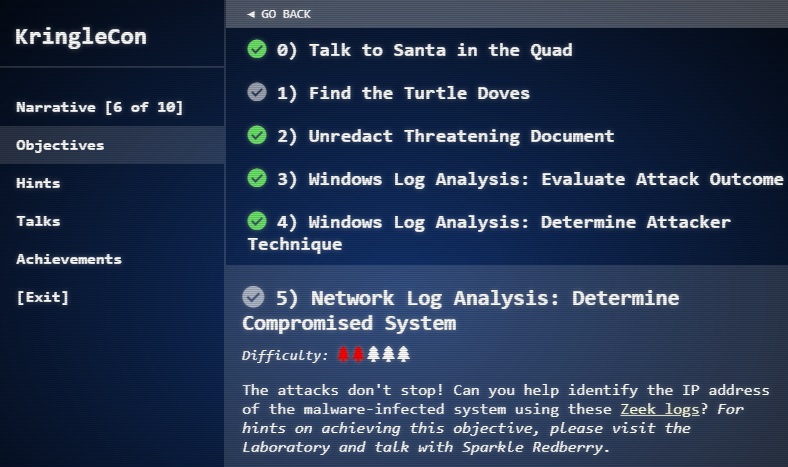
The aim is to solve all the Objectives to help find where the missing turtle doves are. They are ranked in difficulty starting at 1 xmas tree to 4 xmas trees. If you are having trouble with an objective there are helpful elves throughout elf university who will give you a mini-puzzle to solve, these are easier than the objective and if you help an elf with his mini-puzzle they will give you a clue for the main objective.
A lot of the presentations given at Kringlecon also offer hints for the challenges by way of suggesting specific tools and techniques which may come in use for the objectives which works as an extra incentive to pay attention to them all.
If that fails and you are still stuck there is a chat room in the CTF game world full of people who are happy to give hints.
Presentations
There are a treasure trove of talks at Kringlecon by some of the best security minded folk in their respective industries. Even if you don’t use the talks to help with the CTF objectives you will learn plenty just by listening to them all.
There will be more talks released as the event goes on but currently here they all are with a few brief notes about the topics discussed:
John Strand, keynote : A hunting we must go
- The benefits of creating hunt teams whose only task is to identify malware beacons.
- RITA – Real Intelligence Threat Analytics, a tool for identifying malware beacons in traffic.
- Honeybadger – A tool to geo-locate an attacker who has exfiltrated your companies files, works using Googles gigantic wi-fi database instead of IP which can be spoofed.
Katie Knowles – How to (Holiday) hack it: tips for crushing CTFs & Pwning Pentests
- Ways to look at a CTF problem once you get stuck, (has a cool screenshot at 6:07 of a problem spiral.)
- Based on thinking about what new information you have come across since starting the puzzle and new ways of looking at the situation.
Snow – Santa’s naughty list: Holiday themed social engineering attacks
- A look at social and physical attacks which are more likely to succeed during the Xmas holiday season.
- Using the website Glassdoor to see what aspects of a company the staff are emotional about.
- Statistics about e-mail response when using surname, firstname or both.
- Some proactive tips for how to defend against these attacks.
James Brodsky – Dashing through the logs
- An intro to searching through events in Splunk
- An intro to Stoq (E-mail traffic analysis tool)
- A massive hint that this may be useful for some of the Holiday hack challenge objectives
Ron Bowes – Reversing Crypto the easy way
- How to hack crypto which has used bad key implementation.
- Ways to identify which crypto is being used based on its output.
- Great demonstration at the end which makes use of the techniques in the video.
- One of the most technical presentations released so far.
Chris Elgee – web apps : a Trailhead
- An introduction to analysing traffic between you and webapps
- How to alter some values for items processed locally
- Good starting point for someone completely new to security who hasn’t ever seen the source code of a webpage
Chris Davis – Machine learning use cases for cybersecurity
- Discussion about how machine learning can be used in cybersecurity
- How Machine learning can help with specific tasks for blue and red teams
- A demonstration of setting up a machine learning program to spot the difference between apples and bananas
- I’ve seen plenty of mentions that one of the holiday hack challenges can be solved using Machine learning so this one may be worth re-watching.
Deviant Ollam – Optical Decoding of Keys
- A very scary presentation showing how to duplicate a physical key based on only a photograph of the key.
- Step by step demonstration for how anyone can do it with the right tools
Dave Kennedy – Telling stories from the North Pole
- How to prevent SOC staff from spotting your attacks.
- SOC picks up thousands of potential attacks, how to make yours blend in with the other false positives.
- Techniques such as altering the name of your variables/files so that if they are Googled the analyst should come across legit pages for their use.
Mark Baggett – Logs? where we’re going we don’t need logs
- Guide to the built in logging features of Windows 10.
- SRUM-DUMP – A tool for looking at the System Resource Utilisation Management Database.
- ESE2CSV – Command line version of SRUM-DUMP.
- What to do as a forensics investigator when the client has few or no logs.
Heather Mahalik – When Malware goes mobile, quick detection is critical
- Talk about malware on mobile devices
- Growing field so likely to be seeing more of this in the near future
- Less protected than in-office devices
- UFED physical analyser – forensics tool for digging into malware on mobile devices
John Hammond – 5 steps to build and lead a team of holly jolly hackers
- Hints and tips for building a successful team of penetration testers and security researchers
- Advice such as using practical lessons for most of the training, taking parts in CTFs, gamefy learning as much as possible.
- Keep track of what staff have learned and share with other team members
Lesley Carhart – over 90,000: Ups and Downs of my infosec twitter journey
- Advice on the use of social media for members of the cyber security community
- Most of the advice applies to any user of cyber security who has a following consisting of more than just friends and family
- Lesley has over 100,000 twitter followers so her talk is backed by lots of experience
Soundtrack
Last year the soundtrack from the CTF was so popular that this years has been made available as a download available for download here:
Tunes to hack to!!!